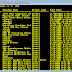
I wrote this today to provide an easy way for anyone to see if a computer is on the network/internet and even do some basic troubleshooting. If someone wanted to take this. Just cut and past into a text file and save with a .bat extension and you should be good to go. Could easily be put on a floppy or e-mailed to someone to test with..
Here is the basic color command:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
@echo off
::
:: cecho by thomas
::
cecho {00}**********{\n}
cecho {0C}{\n}
echo This is a private system operated for HXXX Company business.
echo Authorization from XXX management is required to use this system.
echo Use by unauthorized person is prohibited.
cecho {00}**********{\n}
cecho {0C}{\n}
echo WARNING: This computer system is accessed by authorized users outside
echo of HP. All security and control procedures must be strictly followed.
pause
cecho {00}**********{\n}
echo Unpacking cecho utility
call :unpack_cecho
cecho {00}**********{\n}
cecho {0E}***************************************{\n}
cecho {0E}** BKKGCAP01.asiapacific..net **{\n}
cecho {0E}***************************************{\n}
cecho {0B}{\n}
cecho {9F} ------- {9F}Location: Row {9F}2 {9F}Rack {9F}8 {9F}------ {\n}
cecho {0B}{\n}
ping bkkgcap01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0A}**************************************{\n}
cecho {0A}** TLAEXC01.asiapacific.xxxx.net **{\n}
cecho {0A}**************************************{\n}
cecho {0B}{\n}
cecho {9F} ------ {9F}Location: Row {9F}2 {9F}Rack {9F}2 {9F}------ {\n}
cecho {0B}{\n}
ping tlaexc01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0E}***************************************{\n}
cecho {0E}** BKKFILE01.asiapacific.xxxx.net **{\n}
cecho {0E}***************************************{\n}
cecho {0B}{\n}
cecho {9F} ------- {9F}Location: Row {9F}2 {9F}Rack {9F}1 {9F}------ {\n}
cecho {0B}{\n}
ping bkkfile01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0A}**************************************{\n}
cecho {0A}** BKKCOE01.asiapacific.xxxx.net **{\n}
cecho {0A}**************************************{\n}
cecho {0B}{\n}
cecho {9F} ------ {9F}Location: Row {9F}2 {9F}Rack {9F}1 {9F}------ {\n}
cecho {0B}{\n}
ping bkkcoe01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0E}**************************************{\n}
cecho {0E}** THACOE01.asiapacific.xxxx.net **{\n}
cecho {0E}**************************************{\n}
cecho {0B}{\n}
cecho {9F} ------ {9F}Location: Row {9F}2 {9F}Rack {9F}* {9F}------ {\n}
cecho {0B}{\n}
ping thacoe01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0A}***************************************{\n}
cecho {0A}** THNCIU01.asiapacific.xxxx.net **{\n}
cecho {0A}***************************************{\n}
cecho {0B}{\n}
cecho {9F} ------- {9F}Location: Row {9F}1 {9F}Rack {9F}8 {9F}------ {\n}
cecho {0B}{\n}
ping thnciu01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0A}**************************************{\n}
cecho {0A}** BKKSQL01.asiapacific.xxxx.net **{\n}
cecho {0A}**************************************{\n}
cecho {0B}{\n}
cecho {9F} ------ {9F}Location: Row {9F}2 {9F}Rack {9F}8 {9F}------ {\n}
cecho {0B}{\n}
ping bkksql01 -n 5
cecho {00}**********{\n}
cecho {00}**********{\n}
cecho {0E}*************************************{\n}
cecho {0E}** BKKDP01.asiapacific.cpqcorp.net **{\n}
cecho {0E}*************************************{\n}
cecho {0B}{\n}
cecho {9F} ----- {9F}Location: Row {9F}1 {9F}Rack {9F}8 {9F}------ {\n}
cecho {0B}{\n}
ping bkkdp01 -n 5
pause
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~